11-3: Using TrueCrypt
11-3: Using TrueCrypt
For this practicals, we will be using third party applications that can be downloaded to protect files with cryptography.
Download the application from here.
After downloading, install the program.
Run TrueCrypt and click No to skip tutorial.
Click 'Create Volume'.

Select 'Create an encrypted volume file container'.

Click Next until Volume Size.
Put Volume Size as 1MB and click Next.

Click Next till you reach Volume Format.
At Volume Format, move your mouse for at least 30 seconds to ensure that you will get a strong encryption keys.
Click Format and we have done creating the volume.

Now we are going to mount the contain as a volume.
At the main windows, select an empty drive letter.
Click 'Select File' and navigate to where the container is saved.
Click 'Mount'.
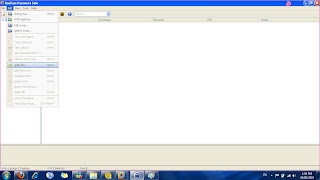
You should get the end result as the picture below.

Remember Encrypted.docx and Not Encrypted.docx?
Save this two files into the TrueCrypt container.
Open them from the container.
Is there a differences in the time to open these two files?
After you are done with this, click 'Dismount' to stop the container.
I think this is quite safe as this is like a hidden folder to keep files just that in this case it is a hidden volume. It also encrypts files that are placed in this volume.