4.1
Practical 4-1: Using the Wireshark Protocol Analyzer
First, download wireshark from www.wireshark.org
Install it.
A protocol analyzer (Also known as a sniffer) captures packets to decode and analyze one or more protocols into a human-readable format for the network administrator. It can also store packets on disk for further analysis later on.
http://www.answers.com/topic/packet-sniffer
In this practical, I am going to connect to a fake FTP connection.
Run the wireshark.
Click Capture > Interfaces > Start
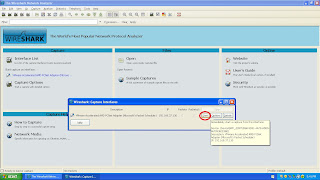
Go to Start, type cmd and press enter.
Type ftp server1.
Packets will then appear on the wireshark.
Type exit and press enter and close cmd.
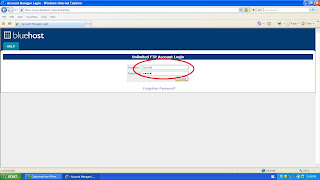
Open IE and go to www.bluehost.com/cgi-bin/uftp
Type in Gerald in username and happy for password.
It will display invalid as it is a fake account.
Then I went back wireshark and search for Gerald. And the information of bluehost.com is been found.
I think that this is actually most dangerous tool as it actually shows packets of information in forms of codes to the attacker.

0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home